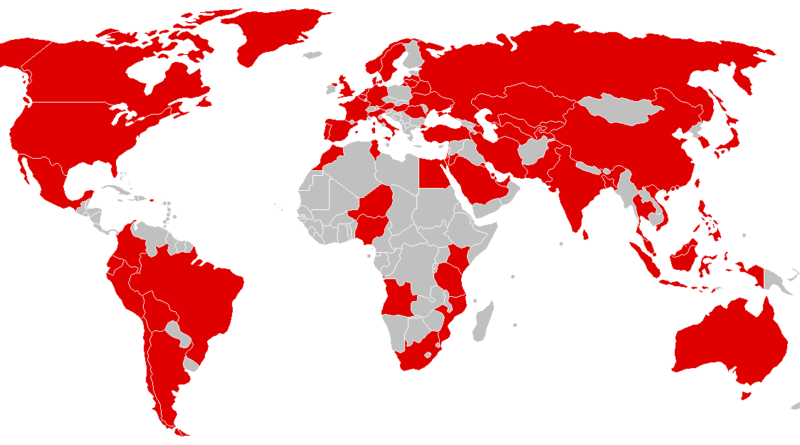
WannaCry Ransomware Spreads Across the World
WannaCry, a fast-moving and devastating new strain of ransomware, has infected computers in at least 150 countries. The malware’s most prominent victims so far are FedEx, Britain’s National Health System (NHS), and Spanish telecom giant Telefónica.
WannaCry Ransomware Exploits Windows Vulnerability
According to The Guardian, an anonymous NHS worker said the ransomware infected a computer on their network after an employee opened a spam email attachment. Hiding malware in Word documents or PDFs attached to emails is typical of cyber attacks.
What has made WannaCry particularly devastating is its ability to spread laterally through a network. After the ransomware infects a computer, the malware spreads to other machines on the same network that have not patched a critical vulnerability. This unique feature is what allowed WannaCry to affect such a large swath of the world.
After a computer in Lancashire, England fell prey to WannaCry, the ransomware spread to the other computers at that location, and then to at least 46 other locations across Britain. Dozens of other organizations had similar nightmare scenarios due to WannaCry.
NSA Tool Used by Hackers
In April, a hacker group called the Shadow Brokers published various tools the U.S. National Security Agency created to target vulnerabilities in Windows operating systems. It is unclear how the Shadow Brokers obtained the information, but now that they’ve published it, hackers around the world have access to these powerful tools.
Microsoft (possibly having been tipped off by the Shadow Brokers) published a patch that protected computers from these exploit kits. Unfortunately, anyone who didn’t apply the patch or who used an unsupported version of Windows was at risk.
Britain’s NHS was particularly vulnerable because they still have many machines using Windows XP, which is no longer supported by updates. Microsoft took the unusual step of releasing a patch for the unsupported operating systems Windows XP, Windows 8, and Windows Server 2003 the day after WannaCry hit.
An Accidental Hero Pauses the Attack
A security expert known as Malware Tech on Twitter, perused the code of WannaCry and noticed a URL. When he went to the website, he realized it was unregistered. He quickly bought the domain for just under $11, hoping he could analyze the spread of the ransomware through it.
This simple act turned out to be a kill switch for the ransomware. There are competing theories as to why the developers of WannaCry built this into the code, but for a short time the ransomware quit spreading. Newer versions without the kill switch have since popped up, but they aren’t functioning as well, and the spread is slowing.
Assessing the Damage and the Profits
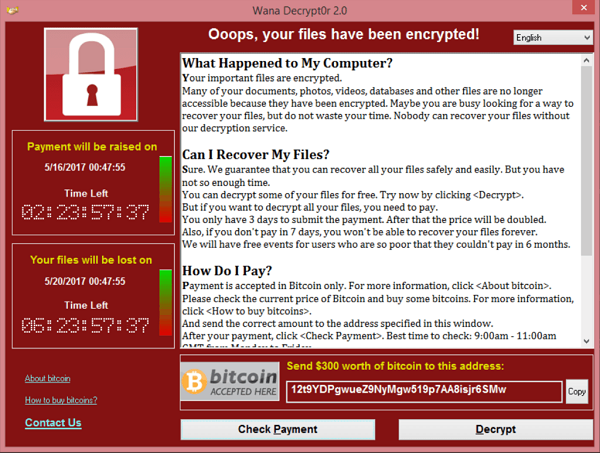
WannaCry demanded a $300 ransom per computer to restore files for victims. By finding the address of the bitcoin wallets in the code, researcher Keith Collins is tracking and updating the profits made off the attack. At the time of writing the total is nearing $54,000.
That number is surprisingly low given that the malware spread to hundreds of thousands of machines in over 150 countries. The ransom note threatens to double the ransom after three days, so we could see payments spike as that deadline approaches for many victims.
The damage to the companies and organizations is exponentially larger than the hackers’ profits. Britain’s NHS cancelled hundreds of appointments due to the crisis and French automaker Renault is shuttered until they debug their computers, and this crisis has just begun.
Avoid WannaCry by Patching (and Using Commonsense)
Anyone who has not updated their Windows operating system should do so immediately by visiting the Microsoft Download Center. This patch prevents WannaCry and other malware from spreading to a machine from infected machines on the same network.
However, this does not make a computer immune to the ransomware. WannaCry can still infect a computer by traditional means, such as through an email attachment.
To avoid WannaCry and other ransomware, never click on suspicious links or attachments in emails. Always back up your files and run an antivirus program. The enormous damage done by WannaCry shows just how quickly ransomware can ruin your day.