Hidden Tear Ransomware Gets Out of Hand
Variants of an open-source, educational strain of ransomware called Hidden Tear have shown up around the world after its creator posted the source code to GitHub. Turkish programmer Utku Sen intended for other programmers to use the malware for educational purposes, but soon, modified versions of the ransomware began infecting computers.
Sen has since taken the code down, but not before it was widely distributed. Sen’s code provides the backbone for at least a dozen strains of ransomware.
Hackers Modified and Improved Hidden Tear
Using the Hidden Tear source code allowed hackers to have a major head start in developing variants of the ransomware. Without doing any of the original legwork, they could add features and graphics to Sen’s malware to make distinct new variants.
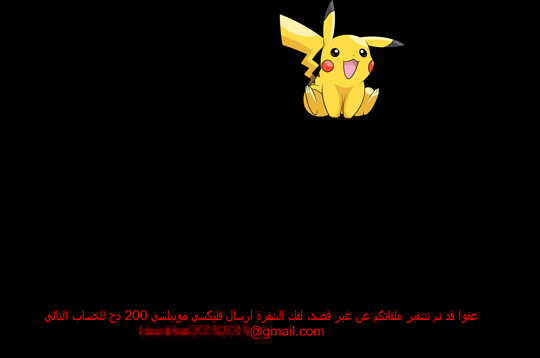
For instance, POGO Tear is a variant that poses as a Pokemon GO app. When users download the malware, it begins to encrypt all of their files. The ransom note features a smiling Pikachu and the demand is written in Arabic. Thankfully, instructions for removing POGO Tear are available from Trend Micro.
The MoWare variant has several modifications from the original Hidden Tear code. It uses a different encryption algorithm and targets very specific folders for encryption. The developers of MoWare also added a Frequently Asked Questions section to the ransom note to help explain the situation to victims.
Open Source Code and Ransomware-as-a-Service Accelerate Attacks
Sen’s open source code for Hidden Tear essentially worked as free ransomware-as-a-service. Though he intended to demonstrate how ransomware worked, his example became real ransomware. Here are just a handful of Hidden Tear variants:
In all, there have been over a dozen new variants discovered since Hidden Tear appeared. We should mention that Sen built a backdoor into the program so that decrypting most infected files is possible. This is a good thing because the developers of some of the variants do not have the ability to decrypt the data they encrypted.
Those Who Can’t Code Still Want Ransomware
The large number of Hidden Tear variants proves there is a high demand for functional ransomware. This seems to indicate that ransomware-as-a-service will continue to flourish.
Those who don’t have the technical ability to create ransomware still want to conduct attacks. Because open source projects like Hidden Tear are rare, attackers will have no choice but to use ransomware-as-a-service if they can’t create their own malware.
Avoiding Hidden Tear Variants
There are so many variations among the variants that it’s hard to avoid them specifically. As always, keep current backups and avoid suspicious attachments and links (we can add apps to this list as well).
Always update your software and avoid clicking anything that looks suspicious. If you are hit, be sure to check out a data recovery company. Remember, you’re not paranoid if they’re really after you!

Like!! Really appreciate you sharing this blog post.Really thank you! Keep writing.