Petya Ransomware Hits Ukraine Hard
A sophisticated strain of ransomware known as Petya has crippled organizations and companies throughout Europe and much of the world. The malware has hit Ukraine the hardest, and security experts are raising questions about the true intent of the malware.
Petya or NotPetya?
The attacks occurred on June 27, and security experts were quick to identify the malware as being related to Petya ransomware, which first showed up in March, 2016. However, the new variant had major enough differences that Kaspersky Labs dubbed it NotPetya or ExPetr.
The most significant difference from the original Petya is that the new incarnation spread laterally through networks. To achieve this, the malware used the Eternal Blue exploit that WannaCry made famous just over a month ago.
Destruction Disguised as Ransomware
The infections originated in Ukraine, where the ransomware infected computers through an update for accounting software used by the government. This spread the malware to the state power company, Kiev’s main airport, the National Bank of Ukraine, and other crucial Ukrainian institutions. The infection forced workers to monitor radiation manually at the Chernobyl Nuclear Power Plant when systems went offline there.
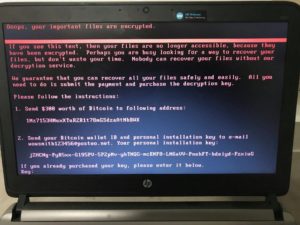
Experts are now suggesting that the Petya/NotPetya attacks were not part of a get-rich-quick scheme, but rather a politically motivated attack on Ukraine. The combination of sophisticated malware with an inept payment system led many to believe that the attackers simply wanted to cause as much destruction as possible.
Ransom Payment Linked to Single Email Address
Petya’s ransom note tells victims to send $300 to a bitcoin wallet, and then send details of the payment to one specific email address. The email provider, Posteo, quickly shut down that address, meaning no one can access or send emails to the address. Because of this, the attackers have no way of knowing who has payed and who hasn’t.
Hackers that have the knowledge to create malware with such advanced capabilities likely would not have relied on a single, web-based email address to receive notifications of payment. Instead, many experts believe that the attackers never intended to make money and decrypt files–they simply wanted to cause destruction and sow confusion by adding the ransom note.
Interpol Investigates
Interpol and the U.S. National Security Council are investigating the attack. In addition to the Ukrainian victims, Petya/NotPetya affected many prominent companies through the world. Here’s a partial list.
- Russian oil producer Rosneft
- Danish shipping company Maersk
- Spanish food conglomerate Mondelez (including an Australian Cadbury’s factory)
- French materials company St. Gobain
- Pennsylvania healthcare provider Heritage Valley Health System
- American pharmaceutical giant Merck
- British advertising company WPP
The wide swath of companies ensures that there will be motivation for uncovering the origin of the attack.
Protecting Your Computer From Petya
While the spread of Petya has slowed, there are still common-sense precautions you can take. Update your Windows operating system with the critical patch that Microsoft released. Always keep software up to date to patch vulnerabilities.
Never click on suspicious links or attachments in emails. Always regularly back up your files so that you have recent copies if a ransomware infection hits your computer. The attacks are getting nastier and more frequent, so taking measures to protect yourself is more important than ever.
