Ukrainian Police Seize Servers from June Cyberattack
Ukrainian Police have seized servers from what they believe is the origin of the worldwide cyberattack in late June. Reporters popularly referred to the malware used in the attack as Petya, NotPetya, or Pnyetya ransomware. However, as researchers analyze the source code, they increasingly believe that the attackers intended to cause destruction more than make money.
The Outbreak Caused Massive Damage in Ukraine
On June 27th, an update from a hacked Ukrainian tax accounting software began spreading the malware. The sophisticated code used NSA’s Eternal Blue exploit, harvested password hashes, and a fake Microsoft signature to spread through networks and elude detection.
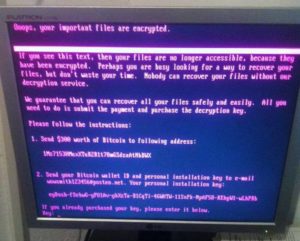
Like typical ransomware, NotPetya encrypted files rendering them unusable. Unlike typical ransomware, the attackers focused more on wiping machines and causing destruction as opposed to holding information hostage and making money.
Sophisticated Source Code, Amateur Payment Plan
Experts now believe that the attackers designed the malware to look like ransomware to cover up the true intention of destroying information and wreaking havoc. The malware used highly sophisticated methods to spread itself and destroy information.
In contrast to that sophistication, the plan for decrypting information was haphazard and underdeveloped. The attackers used just one Bitcoin wallet and one web-based email address to communicate with victims. The email provider quickly disabled the account, meaning victims had no way to communicate with the attackers. Because victims did not have a unique Bitcoin wallet, there was no way for the attackers to know who payed and who didn’t.
Most damning of all was the fact that the pseudo-ransomware’s encryption key is simply a randomly generated sequence of numbers. Multiple security experts concur that there is no way for the attackers to decrypt affected files once the malware fully encrypts them.
NATO Could Retaliate Against Attacks
While Ukraine is not part of NATO, the malware spread to a number of countries who are NATO members, including the United States, France, Germany, Italy, the United Kingdom, and Poland. Many were quick to suspect Russia as the culprit due to their recent conflict with Ukraine and the fact the attacks seemed to target Ukraine specifically.
No one has proven a clear Russian link, but given the large number of companies affected, a thorough investigation will certainly occur. A big first step occurred when Ukrainian Police seized servers from Intellect Service, the IT company behind the accounting software that spread the malware.
Intellect Service Helping Authorities Unravel Chain of Events
After denying that their accounting software was responsible for the spread of the NotPetya malware, Intellect Service is finally cooperating with the police. They admit no wrongdoing and insist that any hacking of their product was done without their knowledge.
Experts have reported “glaring security vulnerabilities” in Intellect Service’s servers and are confident that the accounting software firm spread the malware (whether they knew about it or not). Unfortunately, linking the attacks to Russia or any specific group could be impossible.
Mark McArdle, chief technical officer at eSentire told The Guardian, “Finding irrefutable evidence that links an attacker to an attack is virtually unattainable, so everything boils down to assumptions and judgment.”
