Globe Imposter Variants Have Many Forms, No Decryptor
Globe Imposter ransomware hasn’t matched the major impact of WannaCry or NotPetya, but it’s still making a splash. Infections from Globe Imposter variants have slowly but steadily spread across the U.S., Europe, and the rest of the world. And like many strains of ransomware, there’s no known decryptor.
Staggering Number of Globe Imposter Variants
The most notable quality of this ransomware is its sheer number of versions. Variants encrypt a victim’s files and append them with a variety of extensions. Some of the known extensions are .490, .492, .707, .725, .726, .(email).BRT92, .crypt, .FIX, .GOTHAM, .HAPP, .keepcalm, .medal, .ocean, .pizdec, .rose, .sea, .skunk, ..txt, .vdul, .wallet, and !your_files!.html.
The wide variety of appended extensions makes identification difficult for some victims. A website that detects hundreds of strains of ransomware, ID Ransomware, can determine if Globe Imposter has infected your computer. The free website analyzes the ransom note, an encrypted file, or an email address associated with the malware.
Many Variants Means Many Ransom Notes
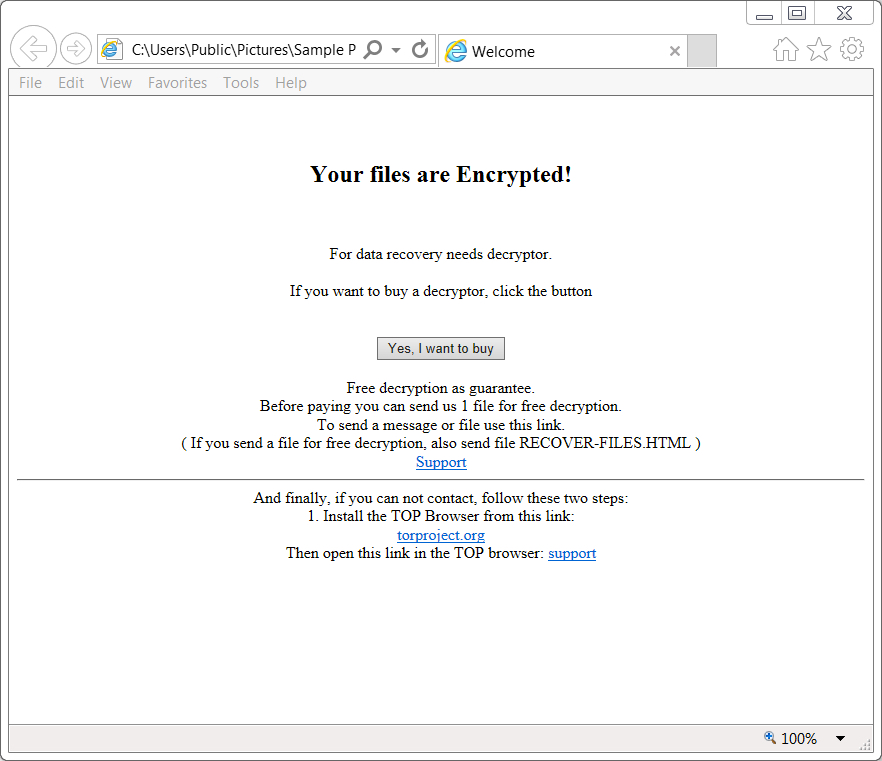
A cursory scroll through #GlobeImposter tweets shows that there is no single ransom demand. Some variants demand the equivalent of $1,000 in Bitcoin. Others ask victims to email the attackers for the ransom amount. Some ransom notes claim that the attackers will only keep the decryption key for 72 hours—after that, a victim’s files will be permanently inaccessible.
Unlike WannaCry and NotPetya, Globe Imposter variants do not spread laterally through networks using Eternal Blue. There have not been any high-profile victims like hospitals or manufacturers. That’s good news, but little solace for victims, whose files remain inaccessible.
No Decryptor for Globe Imposter’s Many Forms
Currently, there is no decryptor for Globe Imposter variants. Instead, victims must rely on backup copies of encrypted files. Most of the ransom notes offer to decrypt one to three files for free to prove the attackers have a working key, but authorities discourage paying ransoms.
Due to the many variants, the ransomware spreads in a variety of ways. The most well-known vector for spreading Globe Imposter is through the “Blank Slate” spam campaign. This campaign distributes malware in emails with blank subject lines and message bodies.
The emails have a zipped attachment that contains a JavaScript function. This script will attempt to download an executable file, which (if run) begins encrypting a computer’s files.
Reasons For Many Variants Unclear
It is unclear why there are so many variants of this ransomware. The attackers might be attempting to hide their tracks or experimenting with effectiveness somehow. Or perhaps the developers are selling the ransomware as a service to different distributors.
Regardless of the motive, the strategy for avoiding Global Imposter is the same as always. Never click on suspicious attachments or links in emails. Always update software. And most importantly, always keep a current backup of your important files.